Thursday, August 7, 2008
CONCEPTUAL RESEARCH & REFLECTION PROJECT
“Good communication practice on the Internet is not something one ‘learns’, but something one ‘practices’ so as to teach others, less familiar than yourself, how it is done.”
Netiquette is defined as the rules and guidelines for online behaviour and it is derived from the words Internet and etiquette (Australian Government NetAlert, n.d.). The internet has become a major part in society as it is a useful tool in collecting information, a form of entertainment and a way in communicating with others. Chat rooms, newsgroups and forums are some examples of the ways individuals can communicate with each other. When communicating online, netiquette is very important since it can have a negative impact on another user. For example, if someone keeps typing in capital letters it is equivalent to the form of shouting and can be offensive to other people who read it. Another example of netiquette is not defaming and abusing people online. Everyone must know that communicating on the internet should have the same manners as when communicating with people offline. However, many people either ignore this or do not take it seriously. On the other hand, there are also a vast number of people who keep their manners when online.
Good communication practice on the internet is not something one learns but something one practices so as to teach others. No one is perfect from the beginning and it obviously takes time and practice to achieve something. Furthermore, if an individual communicates in a good and positive way, others tend to follow. An example of this can be seen through the differences in the design of a website. If a badly designed website and a very attractive website are compared to each another, individuals would tend to go for the attractive site. This clearly shows how the creators of the attractive website have put more effort and input into their work. Meaning, they are better at communicating with their viewers. Through this, the creators of the badly designed website would come to terms that they would need to make modifications and change their site. In this case, the attractive website has opened the road for the badly designed website to grow into a better site.
As mentioned before, when an individual communicates in a positive way others tend to follow. This is an important point since individuals can be easily influenced as well as easily influence others. The internet is a very strong tool that it can be used to influence people in a positive as well as a negative way, depending on how information is communicated and expressed. When the internet was not around, the TV was and still currently is a major tool in influencing and sending information to others. However, now-a-days, the use of the internet has increased dramatically and has become a major influence on many people’s lives. In my opinion, messages should be communicated well and in a good way to receive a positive outcome. Otherwise, it would result in a negative manner. In conclusion, good communication practice allows an individual to share their knowledge for others to see and experience on the internet.
Site 1:
Title: What is Netiquette?http://www.netalert.gov.au/advice/behaviour/netiquette_emoticons/What_is_netiquette.html
This is the Australian Government NetAlert website with information on security, privacy and the more in regards to the internet. I found this site useful in finding the definition and how the word netiquette was derived. This site contains examples of netiquette, a basic and simple list showing the guidelines of how people should and should not communicate on the internet, and it also has information that is short but clearly mentions the important details about netiquette. This is a site that has relevant information on good communication.
Site 2:
Title: Good Practice
http://www.aworc.org/went2001/tracks/t2/t2-good-practice.doc
This is a word document with information in regards to the good practice of using the internet. It contains detailed information on what netiquette is about and the do’s and don’ts of online communication. The document has a clear and easy to read layout, so it was simple to find the information I needed. It also explains how to look make yourself look good on the internet, how to share the knowledge you have to others, how to respect other people’s privacy and more.
Concept 13: Communication is not complete upon receipt
“The key to effective email management is to consistently and conscientiously respond to and act upon the email you receive, while recognising that others may not be as efficient as yourself.”
Email is defined as a system for sending and receiving messages electronically through the internet or a computer network. Emailing is a popular way many people use to communicate with others for personal as well as business use. It is simple to use and it is popular due to the fact that information can be sent immediately to anyone around the world. These are the positive points about emailing but there are also negative issues such as privacy. There are also many times and everyone has probably experienced receiving annoying spam emails.
Although email is used often to send information and to communicate with others, the communication is not complete upon receipt. The reason being is because a person may send an email to another person but if the recipient does not reply back to the sender, then there really is no communication between the two people. The communication has ceased at the recipient’s hands. For a successful communication, information has to be sent back and forth between the sender and the recipient. However, if one of either side does not respond, then there is no communication until a reply is received.
For an effective email management, emails should be responded to in an efficient manner and there are many individuals that do so. However, not all people are the same. In my personal experience, I check my email on a daily basis and when I do receive an email, I respond to it immediately. However, although I replied back very quickly, I have experienced on a few occasions where I waited for a few days until I received a response to the email I sent. In such cases, there is no option but to understand that others may not be as efficient as me.
Furthermore, an email has been sent but the recipient does not respond. There are many times when the recipient may ignore the message and delete it. These are most likely emails from companies advertising and promoting their products, or emails that do not interest the person. Emails can be used to powerfully communicate with others which would assist in avoiding such situations where the recipient simply ignores the email. According to Mind Tools (2008), it mentions how to keep emails short as possible, writing only a few points on what messages needed to be sent, specifying the type of response that is required and more. Long emails tend to appear boring so to avoid this, keeping emails short and precise with a title that informs the receiver of exactly what the email is about will be of great assistance. There are times when you receive an email but don’t have the time to reply back immediately. The best option is to respond and notifying the person that you have received the email and will reply sometime soon. This shows how you have taken notice of the email. These are some of the ways emails can be managed for effective communication with others.
Site 1:
Title: Effective Email
http://www.mindtools.com/CommSkll/EmailCommunication.htm
This is a website which contains useful information on the effective ways of sending emails. It has a list detailing on how to send emails in a way that will make the recipient want to read and respond to the email. It is quite an interesting site to view and gives us an understanding on emailing in depth. It also explains how the use of language plays a major role, in other words, it mentions how you should always check your spelling and try not to use slang.
Site 2:
Title: Managing E-mail Effectively
http://www.3ctraining.co.uk/Management_Voice_Issues/ManagementVoice0009.html
This is a site which is quite similar to that of the above website. It has information on effective email management and these include categorising emails (personal, business, important etc). It also has other hints such as not sending emails when communicating bad news to a person and when in need of giving feedback to do it face to face. This website is useful in knowing more about how to manage your email efficiently and it is also good to know such tips.
Concept 26: Privacy and Security
“The Internet is a profoundly ‘open’ system and advanced Internet users are cautious about either accepting or sending material from and to unknown sources and are careful in releasing information about themselves in any form. Conceptually, the Internet challenges us to take greater responsibility for the protection of privacy and security than perhaps we are used to when dealing with the media.”
The internet is a worldwide system of computer networks where information is sent and received from one another. In the past, the internet was meant for the Advanced Research Projects Agency (ARPA) in the U.S. However, these days, the internet is a public place which is accessible to millions of individuals from all around the world (SearchWinDevelop, 2008). The internet has grown dramatically and it is now a major part in many people’s lives. The email has basically replaced the way of sending mail through post. Most people are more comfortable with sending emails than send a mail by post since it is efficient, convenient and simple. Although there is a convenient point about it, there are also negative issues in regards to sending and receiving information. The internet is too broad to be able to keep all information private and it is difficult to enforce barriers. Viruses and Trojans are basically what make the computer ill and unfortunately, there are people who send such nasty pests through emails.
Advanced users of the internet are careful when they receive information from unknown sources since they have more experience of the internet. Therefore, most people have some type of anti-virus program installed on their computer to prevent and remove viruses off their computer since the internet is not always a safe place. It can be difficult to understand why someone would want to send a virus to another person. Some people send viruses for the enjoyment of it, some people use these viruses to find out personal information for identity theft and to steal information such as credit card details.
Due to such problems, internet users are now becoming much more careful with sending and releasing their personal details online. Using the web, everyone has access to millions of pages of data but there is as much deadly viruses and dangers out there in the open. To prevent unwanted information, viruses and hacking, anti-virus and virus scan programs have been created. Furthermore, there are also other programs which help parents set up a security barrier on the computer to prevent their children from accessing certain sites. On the other hand, several websites have a note where they inform the individual not to release too much personal information when signing up. These points should all be taken into account since the internet world is so vast that you never know what might come at you.
When receiving emails from unknown sources it is essential that you perform a virus check before reading the message. Also, releasing too much personal information can be dangerous since there are many issues in regards to identity theft, that you should always be careful when using the internet. It is the individual’s responsibility to take extra care and thought when online or else they will have to face the consequences.
Site 1:
Title: SearchWinDevelopment Definitions
http://searchwindevelopment.techtarget.com/sDefinition/0,,sid8_gci212370,00.html#
This is a website which contains definitions of the internet and what it is about. It also explains in brief the history and how the internet was formed, how it became public and popular in today’s society. I found this website very useful in finding information in regards to how commonly the internet is being used and accessed by many individuals and how the internet began in the first place. This is a great site to read through for a quick summary on the life of the internet.
Site 2:
Title: How to Be Safe on the Internet
http://www.wikihow.com/Be-Safe-on-the-Internet
This website explains in detail how to be safe on the internet. It is a very useful site and has detailed information and explanations on why and how to be a safe user of the internet. It mentions about emailing, spam, anti-virus programs, chatting, meeting people offline, softwares and more. This website also gives tips on being careful on what you post on the internet since it can have an affect on you when you go for a job interview. There are more useful tips and recommendations on this site.
Concept 22: Public Space and Regulation
“Advanced Internet users are alert to regulatory processes in public discussion and ensure that they do not break them without good cause.”
The online world is a very large space which brings together people from all around the world. Millions of pages of information can be accessed through the internet and you are also able to communicate with people from all different parts of the globe. There are thousands of internet communities that have been created and more being formed everyday. As mentioned before, internet communities allow users of the internet of similar interests to meet and communicate with each other. This is a great way to interact with new people as well as gain information from all different aspects. As much as there are many positive issues about internet communities, the problem that is currently on the rise is the issue in regards to online regulations. The internet and the online world is so huge, it is difficult to make a barrier on everything inside the system. Although creating a barrier may be difficult or even impossible, creating rules and regulations on the community may have some sort of effect. Many people join newsgroups, forums and chat rooms to communicate and integrate with others. In such places, people can be assigned to become moderators who then moderate the community on a frequent basis to make sure that no rules are broken and to help inform members of the guidelines. This allows the community to flow without any hassles and major problems.
First-time users who join an online community will most likely find it confusing and probably will not know the basic regulations of the community. The best way to know what is going on is by overlooking the forum or the chat room and get a better understanding about it before typing and uploading something. Some sites have a regulation where image files are not allowed to be posted due to the fact that it can take up unnecessary data transmissions for other users. For an online community to work out in peace, users must abide by the rules for the safety and sake of other users as well as themselves. If all users co-operate, the longer the online community will last and the less conflicts that will occur.
Regulations in public discussions are essential and it is also vital that internet users do not break them. If they break them, it is most likely that they will receive a first-time warning about the problem, suspension of registration, or even worse, banned from the site. To prevent such situations it is important to cooperate with the website’s regulations. It is also necessary for the makers of the discussion board to set up such rules so that the community does not become out of control. There are many issues where people post unnecessary posts such as spam and unwanted advertisements. This is when the moderators will come into place and clean up the problems. Everyone has the right to express their opinions and thoughts however, when posting a message on a public place, it is essential to abide by the rules. Co-operating and helping the makers of the online community will allow a better flow of the group as well as it will make it easier for you to communicate with others at ease.
Site 1:
Title: New Directions in Cyberspace Law
http://www.gseis.ucla.edu/iclp/sep96.html
This is a great website which explains the history of the internet and how large the internet has grown. It mentions how public the internet has become as well as how it is becoming much more private these days. All individuals have the right to express their opinions and thoughts, and many are doing so online. This website shows how there is a limit on the laws that surround the internet since the online world is so large, it is impossible to create a law for all problems. This is a useful site to read about on regulations on certain internet sites.
Site 2:
Title: Anti-Spam Regulations in Korea
http://www.bakercyberlawcentre.org/2003/Privacy_Conf/papers/Day2/Chung_spam.doc
This is in a word document file about anti-spam regulations that was formed in Korea. This shows how spam is a very significant problem all around the world in the online space. This document is useful in understanding what laws and regulations have been put in place to prevent and prosecute those who break the rules. Although this information is from another country, it proves how necessary it is to set up regulations for the online world to prevent unfortunate incidents from occurring.
BIBLIOGRAPHY
Australian Government NetAlert. (n.d.). What is Netiquette?. Retrieved August 2, 2008, from http://www.netalert.gov.au/advice/behaviour/netiquette_emoticons/What_is_netiquette.html
Biegel, S. (1996). New Directions in Cyberspace Law. Retrieved August 3, 2008, from http://www.gseis.ucla.edu/iclp/sep96.html
Chung, H. (2003). Anti-Spam Regulations in Korea. Retrieved August 3, 2008, from http://www.bakercyberlawcentre.org/2003/Privacy_Conf/papers/Day2/Chung_spam.doc
Good Practice (2001). Retrieved August 2, 2008 from http://www.aworc.org/went2001/tracks/t2/t2-good-practice.doc
Management Voice. (2006). Managing E-mail Effectively. Retrieved August 2, 2008, from http://www.3ctraining.co.uk/Management_Voice_Issues/ManagementVoice0009.html
Mind Tools. (2008). Effective Email. Retrieved August 2, 2008, from http://www.mindtools.com/CommSkll/EmailCommunication.htm
SearchWinDevelopment. (2008). Internet. Retrieved August 2, 2008, from http://searchwindevelopment.techtarget.com/sDefinition/0,,sid8_gci212370,00.html#
Wikihow. (n.d.). How to Be Safe on the Internet. Retrieved August 2, 2008, from http://www.wikihow.com/Be-Safe-on-the-Internet
Sunday, July 27, 2008
Module 4: Organising Search Information Task
- URL: http://www.msnbc.msn.com/id/25410941/
- AUTHOR: Peter Svensson
- INSTITUTION: MSNBC
- SUMMARY: This site discusses the issues regarding a tracking system being used for advertisement purposes on the internet. There are concerns over personal information being accessed and passed on without the individual's acknowledgement. In this article, it mentions how a number of companies in the US are testing the tracking system. Many people have complained and raised issues about their personal information being accessed and sent to others that many companies have decided not to even test the tracking system. The internet is a very broad and powerful tool that it can have a negative impact on an individual if it is used inappropriately.
- URL: http://clearblogs.com/internetbusinessbox/
- INSTITUTION: Clearblogs
- SUMMARY: This site talks about how individuals these days are making money online. Some people earning more money online that they work full-time on the net rather than having a 9-5 job. The site explains how selling an item on the internet is the best way in making money rather than placing simple ads online or completing paid internet surveys.
- URL: http://library.music.indiana.edu/music_resources/
- INSTITUTION: William and Gayle Cook Music Library
- SUMMARY: This is a music library with a variety of information including journals and magazines. It is a great site for those wanting to learn more about music, from the history of music up to the ways music is recorded in studios. It is a site with a huge amount of different information.
Tuesday, July 22, 2008
Module 4: Boolean Searching Task
Module 4: Searching the Web
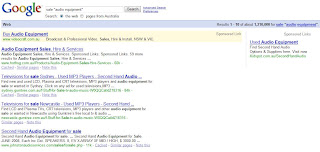
Google.com is the main search engine I use on a regular basis. I did a search on "audio equipment" and these were the results:
 The first hit was titled "Audio Equipment - Australia" and there were 15,200,000 hits in total. (The snapshot below is the first 5 hits from Google!)
The first hit was titled "Audio Equipment - Australia" and there were 15,200,000 hits in total. (The snapshot below is the first 5 hits from Google!)
I then used Copernic to search for "audio equipment" and there was a massive difference in the number of hits compared to what I got from Google. The first hit was titled "Audio Visual Equipment" and there was a total of 79 hits from Copernic.

Here is also a snapshot of the first 5 hits from Copernic:
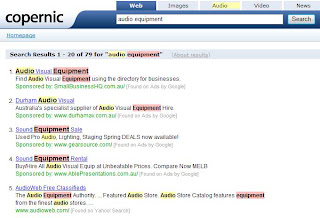
The difference between these two results is the number of hits in total. Google has a much greater number of hits compared to the results from Copernic. To me, both search engines gave information I was searching for. However, from first glance, the results from Copernic appeared to be much more relevant to me. This is obviously due to the fact that Copernic does a more specific search rather than Google.
Thursday, July 17, 2008
Module 4: Tools for Using the Web
- Adobe's pdf reader
I already had this program downloaded and installed on my computer. This is a very useful program since there are many documents online that are created in pdf format. - Flash/Shockwave Players
I visited the Adobe website to see if I had Flash and Shockwave. It confirmed that I had Flash already installed but there was no sign of Shockwave. I then installed Shockwave immediately. I thought I had both on my computer but I guess I didn't! Now-a-days, many websites contain Flash images so it is important to have this. - Media Players
I already had all three media players (Apple Quicktime, Windows Media Player, and Real Networks Real One) installed on my computer. I've used all three media players before and in my opinion, I prefer Quicktime and Windows Media Player! I rarely use Real One, but it is a media player that should be installed on all computers just in case you come across a Real Player file! - Search Manager/Combiners
I downloaded Copernic Meta for PC since I'm a Windows user! I've never used such a program before so this was something new to me. It was quite interesting to see how you could get so many search results from different search engines by using this one program. This seems like a useful tool when in need to search for lots of information! - Bookmark Manager
I downloaded and installed Bookmark Buddy for Windows. I've been aware of this program but I never decided to install it (I guess it's because I didn't feel the need for it). Using this Bookmark Manager program, it helps organize and keeps track of the sites visited. - Offline Browser/Copier
I didn't have either programs (WebCopier and PageSucker) installed on my computer so I decided to download PageSucker. This is a great program where you are able to save pages from websites so that it can be viewed without the internet. I guess this is a handy tool for the times when you are unable to gain access to the internet!
Monday, July 14, 2008
Module 3: Web 2.0
The difference between the two:
- Web 2.0 is more stylish in design and the layout is well set out.
- The structure of the html version is very basic and the layout/design is quite boring.
- Web 2.0 is easier to view and has graphics whereas the html version has no images and text only. (Too much text can make the eyes tired - that's just my opinion!)
The benefits of the two is that web 2.0 has much more freedom than that of the html version. I prefer Web 2.0 since it has a cool style layout and it's interesting to look at. However, the html version just seems boring.
Module 3: Blogs
- Blogs can be used by anyone - experienced or not, anyone can use it!
- It's simple and easy to use
- You can create your own style and design to meet your needs
- Blogs can be used for personal as well as professional use
- Fun and exciting way to express your opinions and gather information
Blogs can be used in many different ways - Personal or professional.
One of the blogs I visit frequently is a blog by DJ Smith & Wesson (http://www.myspace.com/djsmithandwesson). It is a blog where the DJ uploads his music for all to listen to. I enjoy visiting this site because it has a great vibe and great music! Blogs such as this one can be used in a way to promote one's work - in this case, promoting his music. Blogging can be a great way of advertising and for promotion.
Another blog I found about is http://www.damnimcute.com/. This is a blog site on celebrities - updates on what is going on with them. It's an interesting site to see once in awhile. This blog has many interesting articles and photos.
Now for blogs more on the serious side!
This site (http://www.nevblog.com/) is a financial blog by Neville. It shows how and what he has done to earn money through the internet. He also seems to receive donations from people and uses the money in a very kind way! (Recently he has donated a computer to a library!)
I found this blog quite different from other blogs since it shows how an individual makes money and spends it on charity!
Many blogs are used for articles relating to politics. An example of this is the NY Times Blog (http://thecaucus.blogs.nytimes.com/), it has many articles! Personally, I'm not into politics so.. I find these kind of blogs quite boring. Anyway, blogging is a very useful way of expressing opinions and thoughts. I find blogging easy, simple to use and fun! As mentioned before, there is a variety of blogs containing different informations and topics.
Module 3: FTP
Thanks to our discussion board, I then realised that there was a presentations page created for us to upload our web page!

My web page URL: http://webct.curtin.edu.au/305033_b/student_pres/Group52/index.html
Tuesday, July 8, 2008
Module 3: Legal Issues
There is only 1 image file on my web page and it is an image of a turntable which I found on my computer. The words on the page are all created by myself and does not breach any copyright laws.
Would you be in breach of copyright if you put the Curtin logo at the top of your web page for an assignment?
In order to place the Curtin logo on my web page for an assignment I would need to be given permission from Curtin University before I can use the logo. According to the Curtin Copyright Brochure, it mentions that permission should be requested in writing or email. Once granted, I will be able to put the Curtin logo on my web page without the worry of breaching any copyright laws!
Module 3: HTML Tags
After completing the online tutorial, I then created my own web page.
Here's my nice and simple page:
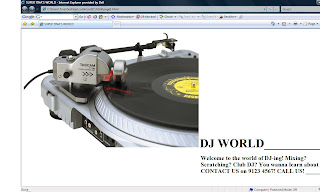
I decided to create a short and simple web page - nothing over the top.
As I was going through the tutorial exercises, I found it quite basic since I've used html before.
I'm not a professional at it but I am quite familiar with html. I found this task straight forward and not difficult at all. The tutorial was an interesting one, it's been awhile since I've used html!
Differences between HTML and blogging:
- Blogging is simple and straight forward - anyone can use it.
- HTML is more advanced and complicated.
- With blogging, you don't really have to go through the hassle of creating templates - they're provided and all you have to do is choose which one you want to use. In contrast, HTML gives you the option of creating and designing your own layout without any barriers. You can create whatever style you desire!
- HTML requires time since you have to type it all out.
I have my own pros and cons on both blogging and html but in the end I prefer using html since you can create your own style and design. With blogging you have a limit on what you can do but with html, you can add so much more. HTML can get boring and time consuming but in the end, I believe the work done through html is much better than that of blogging.
Sunday, June 29, 2008
Module 2: Group Task
MSN LOGO:

mIRC LOGO:

Difference between MSN & mIRC:
- MSN is an instant messenging program where you can chat to one person or as a group.
- mIRC is more used for group chatting but you can chat one on one by 'quoting' them.
- MSN you can add friends so you can chat with them when you go online, you also have the option of emailing fellow hotmail users.
- The layout of mIRC is very basic and simple whereas MSN seems quite modern.
In conclusion, there are a variety of chatting programs out on the internet and they all have similar features but differ in someway. Some are mainly for group chatting, some are for private one on one messenging and so on. As mentioned above, I prefer MSN out of all chatting programs because it is simple to use, nice modern design, there is a vast number of MSN users so it's a popular program and finally it is connected with hotmail so I receive notifications when I receive an email!
Wednesday, June 25, 2008
Module 2: Chat
I downloaded ICQ from http://www.icq.com/download.

I then installed it..

After the installation finished, ICQ popped up automatically.

It's been awhile since I last used ICQ and to be honest, I actually enjoyed using it! I thought I might not like it since I'm used to other chatting programs these days. BUT! It was interesting to use it once again. The difference between ICQ and other chatting programs is that you send short messages to one another. Unlike MSN, where you chat on a single page.
Module 2: Newsgroups
I decided to go to usenet.com.au and then joined aus.music which is a group on music, CDs and radio.
This is the message I posted on aus.music:

This is the first time I've joined a newsgroup and to be honest, I don't think I will ever use it again. I didn't like it on how long it took for a message to show up on the net, unlike discussion boards - they show up immediately! Also, newgroups seemed to be more unorganized and hard to follow. (But that's just my opinion!).
Monday, June 23, 2008
Module 2: Email Lists
http://au.groups.yahoo.com/group/internetstudies/

It's a site that has been made for students currently studying Internet Studies.
Once again, I have never visited such a site before so it was quite a new experience for me.
In order to join the group, I created a Yahoo account (since I couldn't recall the last time I used Yahoo).
Anyhow, after visiting a few sites I began to notice the differences between discussion boards and email lists.
What are the pros and cons of email lists versus discussion boards?
Email Lists Pros:
- Great for distributing information, newsletters, notifications, and more. Simple way of sending information to numerous people - popular way of marketing.
- You don't necessarily have to go to a certain site to view messages since they are sent directly to your email. Convenient way of communicating with others.
- Since you receive all messages by email, you never miss out on what's going on.
- All messages are sent to all subscribers which means that there is an issue with privacy. Information is shared and can be viewed by everyone, so it's not a good option to use email lists if you want to have a private talk with someone.
- Since all messages are sent directly to your email, it can become a nuisance when checking your inbox.
- There is a possibility in receiving spam and junk mail which can be very annoying and harmful to your computer (that is if you get a virus from spam mail!).
Discussion Boards Pros:
- Discussion boards can be viewed as a slow version of chatting. You are able to reply/post messages to certain topics and they are all saved under the topic. Since it's like a slow version of chatting, it's actually quite fun and interesting.
- Useful and simple way of communicating with others. It's quite easy to use and not so complicated. All posts are viewable on a single page.
- Able to build online communities with people of the same interests.
- Popular with many people.
Discussion Boards Cons:
- All posts and replies are viewable by all members who are registered on the discussion board. Basically, there is no privacy!
- Can be inconvenient since you have to go and log in to view the discussion board.
Are there certain kinds of communication or purposes more suited to one than the other?
In a way, discussion boards are much more open and user friendly whereas email lists are very confronting and can be complicating. As mentioned above in the pros and cons, the use of email lists will be much more effective for marketing and promotion purposes. The reason being is that information can be widely distributed directly to subscribers at any time unlike discussion boards where people have to log in and view the messages themselves. On the other hand, depending on how much messages are being sent, email lists can become annoying since it can make one's email inbox full of unnecessary emails.
Discussion boards are popular and easy to use. It is a great way to make an online community and helps bring together individuals with similar interests. Email lists are likely to be used for marketing purposes, whilst discussion boards are more of a place where you can socialize with other people. In my opinion, I find discussion boards more interesting and easier to use. You are able to view a number of messages on a single page, unlike email lists where you have to open and close many windows.
Sunday, June 15, 2008
Module 2: Email Tasks
1. What information about a user's email, the origin of a message, and the path it took, can you glean from an email message?
From an email message we can see who sent the email and where it has come from by simply looking at the email address. An email address consists of a username and domain name ("username@domain"). We can identify the person's name or nickname by looking at the username and the domain name shows where the message is from. For example, if the domain is yahoo.com.au then it is an email supplied by Yahoo in Australia.
The last few letters at the end of an email address helps identify the location or what type of organization it is, for example, .org = organization, .gov = government, .edu = education, .au = Australia, .nz = New Zealand and etc.
Furthermore, we can also see what path the email has taken by looking at the title. Whether it is a reply from a previous message, or a message that has been forwarded to many people.
By looking at an email address we can find out all these informations. It is simple and easy to understand.
2. In what cases would you find it useful to use the 'cc', 'bcc' and 'reply all' functions of email?
CC: This stands for 'Carbon Copy' and it is useful when sending a copy of the same email to someone. It is used to indicate that the email is mainly for the person in the 'To' box, however the 'cc' people may also want to read the email as well.
For example, you send an email to a client and then 'cc' to your boss to show that you have completed the job.
BCC: This stands for 'Blind Carbon Copy' and it is quite similar to the 'cc' function except that the 'bcc' function is discreet. When using 'bcc', the recipient is unaware that other people have received the same email message. This can be useful when you want to secretly send information to a person without the recipient knowing.
For example, you receive threats from an evil person so you 'bcc' the information to the police.
REPLY ALL: This function can be very useful when in need of replying to a number of people with the same message. This saves the time and hassle of typing all the email addresses and it is an efficient way of emailing. When using the 'reply all' function, it replies the same message to everyone that is listed in the email.
3. In what ways can you ensure that an attachment you send will be easily opened by the receiver?
It is important to make sure that the recipient can open the file before sending an attachment. It would be useless if you sent a file that can not be opened. For example, if the file is a word document, the recipient will need a compatible program to open and view it.
If unsure whether the recipient has a compatible program, then sending documents as plain text (ASCII) or as a format that can be viewed by many applications such as Rich Text File (RTF) are another option. File names and file compression should also be taken into account when sending an attachment.
4. What sorts of filters or rules do you have set up, and for what purpose?
The only filter I have currently set up is for spam mail to be received in the Spam Email section. This is a great tool since it separates my email from useless spam mail. Other than that, I do not have any other filters or rules set up.
5. How have you organised the folder structure of your email and why?
The folder structure of my email has been organised into 3 sections - Personal, Business #1 and Business #2. By organizing my emails into different folders helps me from being confused and also allows me to search and find emails that I need to read again quite easily. Without such structuring, all the emails would be mixed up and it would be very frustrating and confusing. Organizing emails into their allocated sections makes everything neat and easy to view.
Tuesday, June 10, 2008
Internet Tools
I then tracerouted to curtin.edu.au and these were the results.

The results I received from centralops was 20 hops in total in 245ms.
I've never used a tool such as traceroute before and it's quite facinating to see how connections can be made quickly to different locations. By looking at the results from centralops, it clearly shows where the connections were made and this shows how broad and deep the internet is.
FURTHER EXPLORATION:
We were also required to ping into the webct site and compare the time taken to ping from my computer and the net tools site (centralops.net). These were the results:

The time taken to ping from my computer to webct.curtin.edu.au [134.7.180.156] only took an average time of 85ms.

From these results, it shows how the location is a major factor in the time taken to ping from one to another. Obviously it took less time from my computer since the distance needed to travel is much less than that of centralops.net. I believe the centralops website is located in America or somewhere overseas and since I'm located in Sydney, Australia, the distance and time taken is much less and faster than that of centralops. I expected these results since I'm in Australia whereas centralops is not.
Next, I tracerouted from my computer to curtin.edu.au [134.7.179.53] and these were the results:
 There was a total of 12 hops in 87ms. Only 12 hops! Centralops.net took approximately 245ms with 20 hops. From these results, it shows how distance is an important factor. The further the distance, the more time it takes to make a connection. On the other hand, the shorter the distance, the less time it takes. This has been quite an interesting task!!
There was a total of 12 hops in 87ms. Only 12 hops! Centralops.net took approximately 245ms with 20 hops. From these results, it shows how distance is an important factor. The further the distance, the more time it takes to make a connection. On the other hand, the shorter the distance, the less time it takes. This has been quite an interesting task!!Friday, June 6, 2008
File Transfer Protocol (FTP) Task

Wednesday, June 4, 2008
Telnet: Task B
Here are a few snap shots of what I saw when I connected to towel.blinkenlights.nl!


Tuesday, June 3, 2008
Telnet: Task A

I then typed library.deakin.edu.au to connect to the library.



Here, I searched for books by the author name of Bennahum. These are the results I received:

I then chose to print both titles to my curtin email.

Finally, I logged into my curtin email account and there it was! The information I had requested had been sent to me! TASK A COMPLETED!!

This was the first time I was experiencing Telnet, and to be honest it was not as complicated as I thought it would be! This was an interesting task and it feels great that I've learnt something new!
Top 5 tips for NEW Bloggers!
1. GOOGLE IT!
Search the internet and see what blog sites are out there! You won't believe how many sites will pop up. (The power of the internet, amazing isn't it?).
2. READ REVIEWS!
Read reviews about certain blog sites, ask friends and people that you know who are into blogging. Getting direct information and opinions from people that you know can be quite useful! Take their recommendations into thought!
3. TEST IT OUT
To get a better feel of the site, register and test it out. See if you feel comfortable with the tools available. If you find it too complicated and difficult to use, try another blog site! Eventually you'll find one which will meet your needs!
4. DESIGN
Once you've created your blog site, it's now for the important part of designing your blog! Some people like it nice and simple, some people like to make it creative and full of design. Create a style that suits you!
5. POST POST POST!
The most vital part of blogging: POSTING!! If you don't post.. I guess there's no point in making a blog site in the beginning. Always be careful on what you write because it's not just only you and your friends but other users of the internet may be able to access your blog. Privacy is a sensitive issue so don't forget that! Remember, post post post! And have fun!


